Herky Crypto Challenge - 2
Herky Crypto Challenge - 2
1a213 d3eb8 a6b16 f799c 61539 f27af 529ab b1f51
85ef1 68536 a7f6b f0e2c e1dde 44885 fd058 c86be
dac0e c2a0e 45764 b7755 f8bcd 51d36 257e7 bc39d
2019a 97850 77525 77e5c 8b66f a581a 4ff59 64854
97d20 2bd44
102b2 67aeb affe6 e7080 35118 e68ee 09c1e e1217
d2fe5 fd563 e0bfe f0e63 b5c6f 95ad7 e4409 09bff
c9cda 97f13 49605 87747 e2fdd d1472 6a682 9d896
204a9 23d41 7d471 b584a d275f c5e58 2cf98 5455f
95d50 bbf44Metadata-less Encrypted Chat Using Axolotl+Tor
Metadata-less axotor
axotor is a command-line chat utility that uses the Axolotl (aka double ratchet) protocol for forward-secret, future-secret, deniable communication. All communication is carried out over the tor network, so there is absolutely no metadata to be surveilled either! Further, all hidden service parameters (keys, onion addresses, etc.) as well as the axolotl key database are stored only in ram. None of this information is ever written to disk! When you quit the chat client and shut down your computer, all of that information disappears forever. This post is an attempt to illustrate axotor's use.
Key exchange between server and client instances is extremely simple. Both both users (we'll call them bob and doug) need to securely agree on a master key via some out-of-band method. The key needs to be of the form NNN-xxxx where NNN is an integer, and xxxx is a complex alphanumeric string. For example, 93-xyz1zy would serve as a key (don't use this one). The integer and the string are separated by a hyphen.
axotor uses this master key to: 1) exchange various credentials such as the address of the server's onion, the onion's authentication cookie, and a ratchet key, and 2) to create the original Axolotl key databases. Credential exchange takes place using password-authenticated key exchange (PAKE). The python magic-wormhole module supplies PAKE functionality. The exchange of credentials takes place over the tor network as well.
There is a nice video (15MB in size) of axotor usage.
Installation is straightforward (although if you want to skip the installation steps and just try it out, go here). Axotor requires the pyaxo, pysocks, txtorcon, stem, and magic-wormhole python modules to be installed. These are available on pypi and can be installed with the command:
sudo pip install pyaxo pysocks txtorcon stem magic-wormholeaxotor.py can be found in the /usr/share/pyaxo/examples subdirectory. To link axotor and its supporting modules in the /usr/local/bin directory, execute the following commands:
sudo ln -s /usr/share/pyaxo/examples/axotor.py /usr/local/bin/axotor
sudo ln -s /usr/share/pyaxo/examples/smp.py /usr/local/bin/smp.py
sudo ln -s /usr/share/pyaxo/examples/wh.py /usr/local/bin/wh.pyAfter you have installed axotor, usage proceeds as follows (click the thumbnails on the terminal images for a larger version of each image):
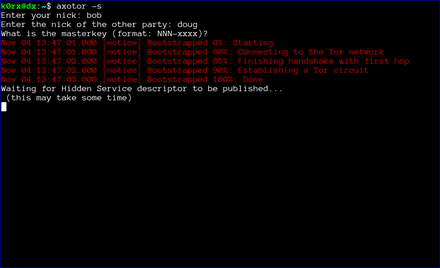
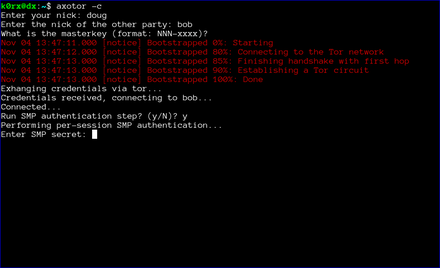
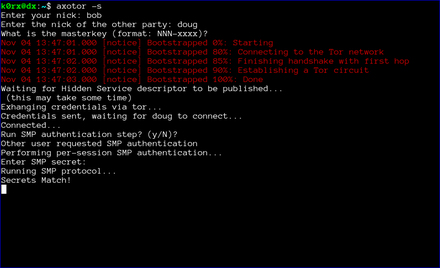
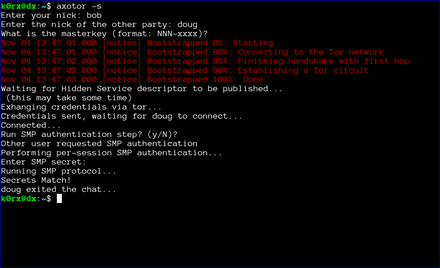
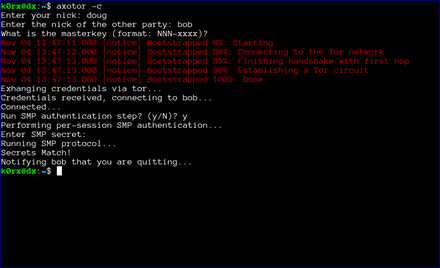
The first step is for both users to start axotor. One user starts as the server using axotor -s (left-side images) and the second user starts as the client axotor -c (right-side images).
Each user selects and enters a nickname.
Each user then enters the nickname for their communication partner.
Finally, each user enters the previously agreed-upon master key.
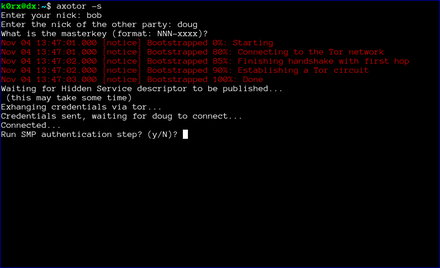
The server then proceeds to create a tor hidden service. axotor will wait until the hidden service descriptor is published before returning (this usually takes about 30 seconds or so).
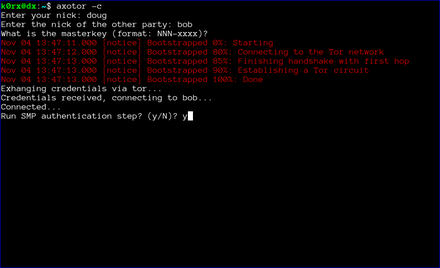
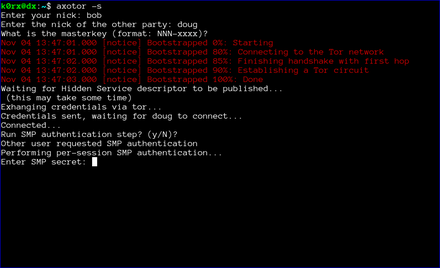
axotor will then ask if either user wants to go through a socialist millionaire's protocol authentication process. In the example below, bob chose not to, but doug wanted to. As a result, axotor will require SMP authentication. If neither user wanted to go through the SMP authentication step, axotor will skip it and go directly to the chat window. Obviously, if both users request SMP, axotor will execute the protocol as well
axotor then asks for the authentication secret. This should be an additional secret agreed to out-of-band by the two users.
axotor notifies each user of the success or failure of the SMP step.
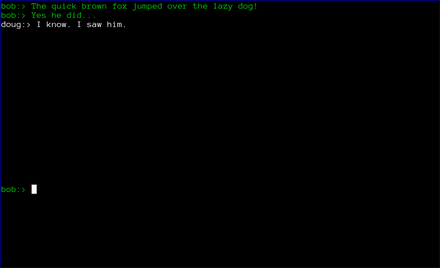
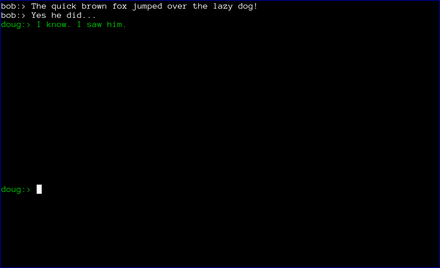
Finally, the chat window opens. Green text signifies that either the SMP step was successful, or that the users chose to skip that step. If the the SMP step is not successful, the users will be prompted to exit. If they choose not to, the text will appear red to remind them that the SMP step was unsuccessful.
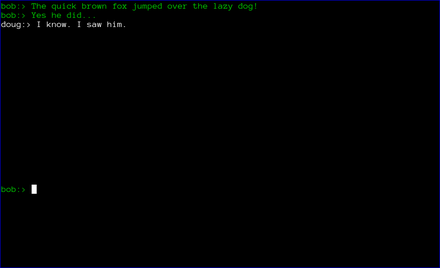
At this point, axotor acts like every other chat client. The users can exchange messages as they wish. Each message is encrypted with a different key, with what is widely recognized as the most secure messaging protocol available (Axolotl).
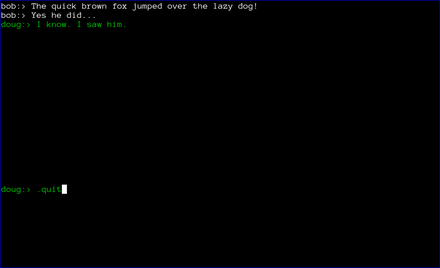
Finally, when the chat is over, either user can type .quit to exit the chat. In the case shown below, doug chose to quit.
axotor then notifies bob that doug has quit the chat and shuts down the chat window.
End Notes
The axotor server and client instances use different ports for their tor servers, so it is very easy to try axotor out. You can run the server and client side by side in two different terminal windows on the same machine.
If you want to try axotor out without going through all the installation steps, there is a docker image I created to do that. Execute the start.sh script from the unmessage-client repository and this will download and run the docker image. At the docker container's bash prompt, proceed with the commands axotor -s or axotor -c as appropriate.
We also want to emphasize that the code has not been audited. Please do not use axotor for any activity that your life depends upon!
Postscript
The file-transfer branch of the pyaxo github repository has the capability for encrypted file transfer as well.
Edit: encrypted file transfer is now enabled in master branch.